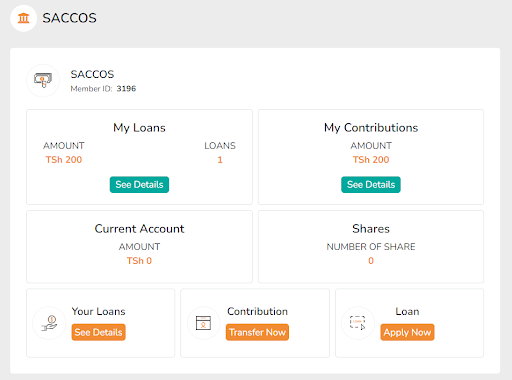
Wakandi Launches Series A Round to unlock the African economy
Nairobi, 13 May 2025—At a private gathering hosted by the Norwegian Ambassador in Nairobi, Wakandi officially launched its Series A capital raise, marking a bold new chapter in our mission to...